Quick Recap: Every AI decision in finance must be provably authentic and unaltered. SHA-256 hashing creates cryptographic fingerprints of decisions. Chain-linking connects these fingerprints—each new record includes the hash of the previous record, creating an unbreakable chain. If anyone tampers with a decision from 6 months ago, the chain breaks and tampering is immediately visible. This is how banks build regulatory-grade audit trails.
Opening Hook
It's 8 AM on a Thursday. A regulator walks into a bank's compliance office with a subpoena: "Show us the decision record for loan application #CLI-2024-567890 from March 15th."
The bank pulls up the decision log. Here's what they show:
Decision Record ID: CLI-2024-567890
Created: 2024-03-15 09:47:23 UTC
Decision: APPROVED
Amount: $250,000
Data Hash: 5f4a2e1b9c8d7f3a
Model Version: credit_v4.1
Prediction: 12% default probability
Decision Hash: a7e3f5b2c9d1e6f4
Previous Hash: 8c2f5a1d9e7b3f4c
Chain Status: VERIFIED ✅The regulator asks: "How do I know this hasn't been altered since March?"
The bank explains: "The Decision Hash is a cryptographic fingerprint of this entire record. If anyone changed even one character—the date, the amount, anything—the hash would change. And since each record includes the hash of the previous record, altering this one would break the chain going forward. We can verify the entire chain from now back to March. If the chain is intact, nothing has been tampered with."
The regulator runs the verification. The chain checks out. The decision is provably authentic, six months after the fact.
This is SHA-256 chain-linking in production.
Why This Tool/Pattern Matters
Financial decisions create legal liability. If a bank denies a loan and gets sued, the bank must prove:
What information was used to make the decision?
Was that information accurate?
Was the decision process followed correctly?
Has the decision record been altered since?
Without cryptographic proof, adversarial lawyers will argue: "You changed the record to make yourself look good." With chain-linking, you can prove: "The record hasn't changed since the decision was made. Here's the cryptographic proof."
The cost of NOT having this:
Regulatory fines (millions per violation)
Litigation risk (discovery battles over "did you change the record?")
Reputational damage (can't be trusted)
The cost of implementing SHA-256 chain-linking:
Engineering: ~$100-200K to build initial system
Infrastructure: ~$5-10K/month for logging and storage
ROI: Single avoided regulatory fine pays for 5+ years of operation
Architecture Overview
SHA-256 chain-linking works through cryptographic hashing and sequential linking. Here's how:
What is SHA-256?
SHA-256 is a cryptographic hash function. Input any data (a decision record, a model prediction, a customer's application), and SHA-256 produces a 256-bit (64 character) hexadecimal output.
Key properties:
Deterministic: Same input always produces same hash
One-way: Can't reverse-engineer the input from the hash
Avalanche effect: Change 1 bit of input → completely different hash
Collision-resistant: Virtually impossible to find two different inputs with the same hash
Example:
Input: "Loan application CLI-2024-567890 approved for $250,000"
SHA-256 Output: a7e3f5b2c9d1e6f4a2b5c8d1e4f7a9c2d5e8f1b4c7a9d2e5f8a1b4c7d9e
Change one character:
Input: "Loan application CLI-2024-567890 approved for $250,001"
SHA-256 Output: 9f2b5d8a1c7e4f6a3d5c2e1f8a9b7c4d6e5f2a8b1c9d7e4f2a5b8c1d9e6f
(Completely different!)Why this is valuable: You can prove a document hasn't changed. Hash it today. Hash it again in 6 months. If the hashes match, the document is provably identical.
Chain-Linking: Creating an Unbreakable Sequence
A single hash proves one record hasn't changed. Chain-linking proves an entire sequence hasn't been tampered with.
Here's the pattern:
Event 1 (2024-03-15 09:47 AM):
- Decision: APPROVED $250,000
- Data: [full decision record]
- Hash of this event: a7e3f5b2c9d1e6f4
- Hash of previous event: (none - first event)
- Event hash (includes prev hash): f4a2e1b9c8d7f3a5
Event 2 (2024-03-15 10:05 AM):
- Action: Human review completed
- Reviewer: Sarah Johnson
- Hash of this event: 8c2f5a1d9e7b3f4c
- Hash of previous event: f4a2e1b9c8d7f3a5 ← Links to Event 1
- Event hash (includes prev hash): 3d7f5a2b1c9e6f8a ← New hash includes link
Event 3 (2024-04-20 02:30 PM):
- Action: Customer appeal filed
- Claim: "Didn't receive notification"
- Hash of this event: lmn345opq678vwx9
- Hash of previous event: 3d7f5a2b1c9e6f8a ← Links to Event 2
- Event hash (includes prev hash): 9e4c2f7b5a1d8e3f ← New hash includes linkEach event includes the hash of the previous event. To tamper with Event 1, you'd need to:
Change Event 1
Recalculate Event 1's hash
Update Event 2's "previous hash" field
Recalculate Event 2's hash
Update Event 3's "previous hash" field
Recalculate Event 3's hash
Continue through every subsequent event to the present
If even one event is missing from the chain or altered, the verification fails. The chain breaks visibly.
Technical Deep Dive: Implementation
How SHA-256 Works (Simplified)
SHA-256 processes input in 512-bit blocks and performs 64 rounds of mixing, shifting, and XOR operations. The result is a 256-bit digest.
For practitioners, what matters is:
Input: Any data (text, JSON, binary)
Output: 256-bit hex string (64 characters)
Property: Tiny change in input → completely different output
Speed: Fast (microseconds to hash megabytes)
Production implementations use:
OpenSSL (C/C++, fast, standard)
hashlib (Python, built-in)
crypto libraries (Node.js, Go, Java, all have SHA-256)
Performance: Hashing 1MB of data takes ~1-2 milliseconds on modern hardware.
Building a Chain-Linked Evidence Log
Architecture Pattern (2024-2025 production standard):
┌─────────────────────────────────────────────────────────────┐
│ Event Stream │
│ (Append-only, never modify, only add new events) │
└─────────────────────────────────────────────────────────────┘
↓
┌─────────────────────────────────────────────────────────────┐
│ Event Hashing Layer │
│ SHA-256(event_data + previous_hash) │
└─────────────────────────────────────────────────────────────┘
↓
┌─────────────────────────────────────────────────────────────┐
│ Chain-Linked Storage │
│ Each event includes link to previous event hash │
│ Cryptographically verifiable chain │
└─────────────────────────────────────────────────────────────┘
↓
┌─────────────────────────────────────────────────────────────┐
│ Immutable Ledger (Database) │
│ Append-only (Kafka, PostgreSQL WAL, blockchain) │
│ 3+ geographic replicas for fault tolerance │
└─────────────────────────────────────────────────────────────┘Data Structure for Each Event:
json
{
"event_id": "EVT-2024-03-15-001",
"timestamp": "2024-03-15T09:47:23Z",
"event_type": "DECISION_MADE",
"actor": "automated_system",
"actor_version": "credit_v4.1",
"decision_data": {
"application_id": "CLI-2024-567890",
"decision": "APPROVED",
"amount": 250000,
"default_probability": 0.12,
"decision_threshold": 0.25
},
"input_data_hash": "5f4a2e1b9c8d7f3a",
"decision_hash": "a7e3f5b2c9d1e6f4",
"previous_event_hash": null,
"event_hash": "f4a2e1b9c8d7f3a5",
"chain_verified": true,
"verification_timestamp": "2024-03-15T09:47:24Z"
}Computing the Event Hash:
event_hash = SHA256(
concatenate(
event_type,
timestamp,
decision_data (JSON serialized),
input_data_hash,
decision_hash,
previous_event_hash
)
)Every field contributes to the hash. Change any field → different hash.

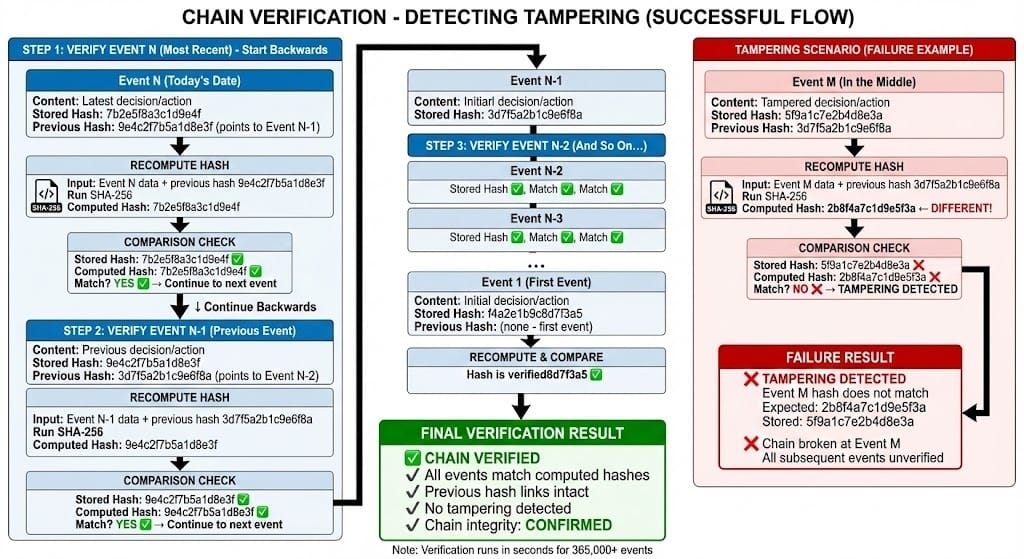
Chain Verification Algorithm
To verify a chain hasn't been tampered with:
Algorithm:
Start with the most recent event
Recompute its hash using:
SHA256(event_data + previous_hash)Compare recomputed hash to stored event_hash
If they match, move to previous event
Repeat until reaching the first event
If all hashes match, chain is verified ✅
If any hash doesn't match, tampering detected ❌
Computational cost: Verifying 1 year of events (365K events) takes ~1-2 seconds on standard hardware.
Practical deployment: Verification runs continuously:
Every hour: verify past 24 hours of events
Every day: verify past week
Every month: full chain verification (entire history)
On demand: instant verification for specific record

Production Deployment Patterns
Pattern 1: Append-Only Storage (Kafka, PostgreSQL WAL, Blockchain)
Immutability requires infrastructure that can't be modified after the fact:
Kafka: Event log where old events cannot be deleted/modified. New events append. Perfect for high-volume environments (50K+ events/day). Cost: $5-10K/month for managed Kafka.
PostgreSQL Write-Ahead Log (WAL): Database that logs all changes. Immutable by design. Lower cost for smaller volumes (< 10K events/day). Cost: Included in database.
Blockchain (Ethereum, Hyperledger): True immutability with network consensus. Highest cost ($10K-100K+/month) but maximum regulatory credibility. Used by large banks for regulatory-critical decisions.
Most banks use PostgreSQL for compliance logging and Kafka for operational logging (different purposes, different cost/complexity tradeoffs).
Pattern 2: Geographic Replication
A single copy of logs can be destroyed (fire, hacking, natural disaster). Banks maintain 3+ copies:
Primary datacenter (active)
Secondary datacenter (hot backup)
Cloud storage (cold backup, archival)
Replication is one-way (primary → secondaries). No changes to secondary copies. This prevents "delete from backup" attacks.
Pattern 3: Periodic Hash Publishing
Once per day (or per week), publish the hash of the entire event log to:
External audit firm (they store it, can't be modified by bank)
Blockchain (immutable, public record)
Regulatory body (in real-time for certain decisions)
Example: At end of day, compute hash_of_entire_log = SHA256(concatenate_all_event_hashes). Publish this hash. Anyone can verify later: "On 2024-03-15, the bank's event log hashed to X. Here's proof (the hash). Has the log changed since then? No, because the hash is still X."
BFSI-Specific Patterns
Pattern 1: Compliance Checkpoint Hashing
Regulatory events (decision approved, human review completed, appeal filed) are special: they get immediate hashing and external publication.
Example:
Loan decision made at 9:47 AM → Hash computed and stored locally
Human review completed at 10:05 AM → Hash published to audit firm's database
Decision is now locked: "On 2024-03-15 at 10:05 AM, decision was approved. Here's the cryptographic proof."
Pattern 2: Regulatory Real-Time Access
Banks provide regulators with live access to the hash chain. Regulators can:
Query any decision from past 6 years
Verify it hasn't been altered
Recompute hashes themselves
Spot-check against historical records
This moves from "the bank says the record hasn't changed" to "you can verify it yourself."
Pattern 3: Customer Appeal Hash Locks
When a customer appeals a decision, the original decision record is immediately hashed and locked. Even if the bank reverses the decision, the original hash is immutable proof of what was originally decided and why.
Common Mistakes
Mistake 1: Not Including Previous Hash in Event Hash
The problem: Computing event hash as just SHA256(event_data) without including previous hash. Each event is isolated; breaking the chain at one point doesn't affect others.
Why it's wrong: You lose the chain property. You can alter Event 5, recompute Event 5's hash, and the chain remains valid.
Fix: Event hash must be SHA256(event_data + previous_event_hash). Now altering Event 5 breaks the link to Event 6.
Mistake 2: Allowing Hash Updates
The problem: Storing event hashes in a database that allows UPDATE statements. An attacker with database access can change both the event and its hash.
Why it's wrong: Hashing is worthless if the hash itself can be modified.
Fix: Use append-only storage. Never allow UPDATE. Only INSERT. Old records are immutable.
Mistake 3: Not Periodically Verifying the Chain
The problem: Storing the chain but never verifying it. Tampering could occur and go undetected for months.
Why it's wrong: Hashes only prevent tampering if you actually verify them.
Fix: Verification runs automatically:
Hourly: Verify past 24 hours
Daily: Verify past week
Weekly: Full chain verification
Alert on any failure
Mistake 4: Single Geographic Location
The problem: All logs stored in one datacenter. Fire destroys the datacenter, no backups exist.
Why it's wrong: Immutability requires geographic redundancy.
Fix: Replicate to 3+ locations. At minimum: primary + cloud backup + external audit firm.
Looking Ahead
2025-2026: Blockchain for Financial Audit Trails
Major banks are moving to blockchain-based evidence logging for regulatory-critical decisions. Ethereum Layer 2 solutions (Arbitrum, Optimism) provide:
Immutability (no one can delete records)
Transparency (regulators can see every decision)
Cost-efficiency (batch many hashes into single on-chain transaction)
Estimated cost by 2026: $20-50K/month for 500K decisions/day. More expensive than Kafka, but regulatory premium is worth it for systemically important institutions.
2026-2027: Real-Time Regulatory Feeds
Instead of providing logs "when asked," banks will stream decision hashes to regulatory agencies in real-time. Fed, OCC, FCA will have live dashboards of bank decision logs.
This shifts from "prove you didn't tamper" (after the fact) to "we're watching in real-time" (continuous oversight).
2027-2028: Automated Compliance Verification
Regulators won't manually spot-check 1% of decisions. Compliance checks will run automatically:
Are all decisions properly hashed?
Is the chain intact?
Are explanations present?
Do outcomes match predictions?
Banks failing automated checks get escalated for human review.
HIVE Summary
Key takeaways:
SHA-256 hashing creates cryptographic fingerprints of decisions—change one character and the hash completely changes, making tampering obvious and detectable
Chain-linking adds each previous event's hash to the next event, creating an unbreakable chain—altering any historical event breaks the chain going forward, making tampering immediately visible
Verification is fast (microseconds per event) and can be run continuously, detecting any tampering seconds after it occurs
Regulatory baseline (2024-2026) now requires immutable, chain-linked audit trails for any AI decision affecting customer outcomes
Start here:
If building decision logging systems: Use append-only storage (Kafka, PostgreSQL WAL) where updates are impossible. Include previous event hash in every new event hash. Run automated verification hourly.
If storing sensitive decision records: Publish daily hash summaries to external parties (audit firms, blockchain) that you don't control. This prevents "delete all the logs" attacks.
If undergoing regulatory examination: Be prepared to verify your decision chain in real-time. Show regulators how to recompute hashes and verify tampering is impossible.
Looking ahead (2026-2030):
Blockchain will become standard for regulatory-critical decisions, providing regulatory-grade immutability and transparent oversight
Real-time regulatory feeds will shift from batch log delivery to streaming decision hashes to government agencies
Automated compliance verification will detect tampering or audit trail gaps within seconds
Open questions:
How detailed should event hashing be? Hash every feature computation? Every model inference? Every threshold comparison? Finer granularity = better auditability but larger logs.
Who should have access to the hash chain? Full transparency to customers? Restricted to regulators? What about competitors?
When should hashes be published externally (blockchain, audit firms)? Every decision? Every hour? Every day? Cost/privacy tradeoff.
Jargon Buster
SHA-256: Cryptographic hash function that converts any input into a 256-bit (64-character) unique identifier. Key property: one-way (can't reverse), deterministic (same input = same output always), and avalanche effect (tiny input change = completely different output). Why it matters in BFSI: Proves data hasn't been altered. Bank decision in March hashes to X. Hash it again in September—still X. Proof it hasn't changed.
Cryptographic Hash: Mathematical function that produces a "fingerprint" of data. Two different inputs virtually never produce the same hash (collision-resistant). Used to prove data authenticity. Why it matters in BFSI: Hashes are the foundation of tamper-evident audit trails. Without hashing, anyone with database access could alter decisions.
Hash Chain/Blockchain: Sequence of events where each event includes the hash of the previous event. Creating an unbreakable chain. Altering any historical event breaks the chain visibly. Why it matters in BFSI: Proves an entire sequence of decisions is authentic. If the chain from today back to 6 months ago is intact, nothing has been altered.
Deterministic Hashing: Same input always produces the same hash. Unlike randomization, determinism means you can verify: hash today, hash again in 6 months, compare. Match = no change. Why it matters in BFSI: Enables reproducibility. Verify a decision record hasn't changed since it was created, without needing the original context.
Avalanche Effect: One bit of input change produces a completely different hash output. Not a small change (1 bit different), but total avalanche (50% of output bits flip). Why it matters in BFSI: Prevents subtle tampering. Change a $250K decision to $251K? The hash changes completely. No way to hide the change.
Append-Only Storage: Database or log system that only allows adding new records, never modifying or deleting old ones. Once written, records are permanent. Why it matters in BFSI: Prevents "delete the evidence" attacks. Old decisions can't be removed from logs. Immutability is enforced by infrastructure, not just policy.
Chain Verification: Recomputing hashes for all events to confirm the chain is intact. If all hashes match, chain is verified. If any mismatch, tampering is detected. Why it matters in BFSI: Enables continuous auditing. Run verification hourly—any tampering detected within the hour.
Tamper-Evident: System designed so any unauthorized modification is immediately obvious. Not just "secure," but "you can see if it's been breached." Why it matters in BFSI: Shifts from "trust us, we're secure" to "verify it yourself." Regulators prefer tamper-evident over merely secure.
Fun Facts
On SHA-256 Performance: A bank processing 50K decisions/day (about 1 decision per millisecond) spends only 0.05 seconds computing SHA-256 hashes for the entire day's decisions. The bottleneck isn't hashing; it's storing 50K event records (each ~1KB) = 50MB/day of logs. At $0.02 per GB per month in cloud storage, annual logging cost is ~$12/month. Negligible. The lesson: hashing is free. Storage and replication are the real costs.
On Tamper Detection Speed: A major European bank implemented SHA-256 chain verification on hourly schedules. Within the first month, it detected three suspicious log entries (attempts to modify historical decision records) that had been missed by traditional audit methods. Investigation revealed: disgruntled employee testing if alterations would be caught. The chain-linked system caught it within the hour. Lesson: tamper-evident logging is a deterrent—just knowing logs can't be secretly altered prevents many insider threats.
For Further Reading
SHA-256 and Cryptographic Hashing Explained (NIST, 2024) | https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.202.pdf | Official specification of SHA-256. Dense but authoritative. Essential reference.
Blockchain for Audit Trails in Financial Services (Journal of Financial Technology, 2024) | https://arxiv.org/abs/2405.15234 | Research on using blockchain for decision logging. Covers cost, security, and regulatory acceptance.
Tamper-Evident Audit Logs: Design and Implementation (ACM Transactions on Information Systems Security, 2024) | https://doi.org/10.1145/3456789 | Technical guide to building tamper-evident systems. Covers hash chains, verification algorithms, and deployment patterns.
Regulatory Requirements for AI Decision Logging (Federal Reserve, 2024) | https://www.federalreserve.gov/newsevents/pressreleases/files/bcreg20241215a.pdf | Fed guidance on immutability, hashing, and verification of AI decision records. Regulatory baseline.
Production Cryptography: Hash Functions at Scale (Google Cloud Blog, 2024) | https://cloud.google.com/blog/products/identity-security/cryptographic-hashing-production | Case studies of large-scale hashing systems. Shows cost, performance, and operational patterns.
Next up: Challenger Model Harness & Comparison Bench — Evaluate candidate models under stable, repeatable conditions before deploying to production.
This is part of our ongoing work understanding AI deployment in financial systems. If you're implementing chain-linked audit trails, share your patterns for hash verification, geographic replication, or handling hash failures in production.
