Quick Recap: When you buy models from vendors (OpenAI, Anthropic, Cohere) or use third-party ML platforms (SageMaker, Databricks, Hugging Face), you inherit their data handling practices. Regulators hold you accountable for vendor behavior—your responsibility doesn't end at contract signature. Financial institutions need frameworks to audit vendor security, data practices, bias testing, and incident response before signing on.
It's Thursday morning. Your fintech is deploying a fraud detection model using a vendor's pre-trained LLM. The vendor advertises "enterprise-grade security" and "GDPR compliant." Your procurement team signs the contract.
Two months later, your compliance officer gets a notice: The vendor experienced a data breach. Customer data was exposed for six weeks before detection. The vendor is now notifying all customers.
Your CEO asks: "We didn't build this model. We licensed it. Whose liability is this?"
Your compliance officer's answer: Yours.
Even though the vendor caused the breach, regulators hold your institution accountable. The Federal Reserve expects you to have audited the vendor's security before deployment. Your risk committee expected due diligence. Your customers expect you to have chosen a trustworthy partner.
You face:
Customer notification requirements
Regulatory investigation ("Why did you choose this vendor?")
Potential fines (regulators hold you liable for vendor risk)
Reputational damage
Three weeks of crisis management later, your board asks: "How do we prevent this?"
This is vendor risk in AI. When you outsource to vendors, you can't outsource accountability.
What Regulators Mean by "Vendor Risk"
Traditional vendor risk (for software licenses, cloud infrastructure) is well-understood:
Assess security practices
Review service level agreements (SLAs)
Audit compliance certifications (SOC 2, ISO 27001)
Test incident response procedures
AI vendor risk adds layers:
Data Handling Risk
Does the vendor train their models on your data?
Do they retain data after service ends?
Where is data stored (jurisdiction matters)?
Can they resell insights derived from your data?
Model Risk
How was the model trained? On what data?
Has it been tested for bias against protected attributes?
What's the model's decision-making logic?
Can you audit individual predictions?
Operational Risk
How do you know when the model has drifted?
What's their incident response time?
Can they push updates without your approval?
What happens if they shut down?
Compliance Risk
Are they GDPR/CCPA compliant?
Do they comply with your jurisdiction's regulations?
What audit rights do you have?
How do they handle regulatory requests?
Regulators expect you to have answers before signing contracts.
The Three Vendor Categories
Category 1: Model Vendors (OpenAI, Anthropic, Cohere)
You: Send data → Receive predictions
Vendor: Hosts model, processes your queries
Risk level: High (your data passes through their systems)
Control: Limited (they control model updates)
Category 2: Platform Vendors (AWS SageMaker, Google Vertex, Azure ML)
You: Train your own models on their infrastructure
Vendor: Provides compute, storage, tooling
Risk level: Medium (your data stays in their environment)
Control: High (you build and deploy your models)
Category 3: Component Vendors (Hugging Face, TensorFlow models)
You: Download pre-trained models, fine-tune locally
Vendor: Provides model code/weights
Risk level: Medium (depends on model training data)
Control: High (you control deployment)
Each category requires different due diligence.
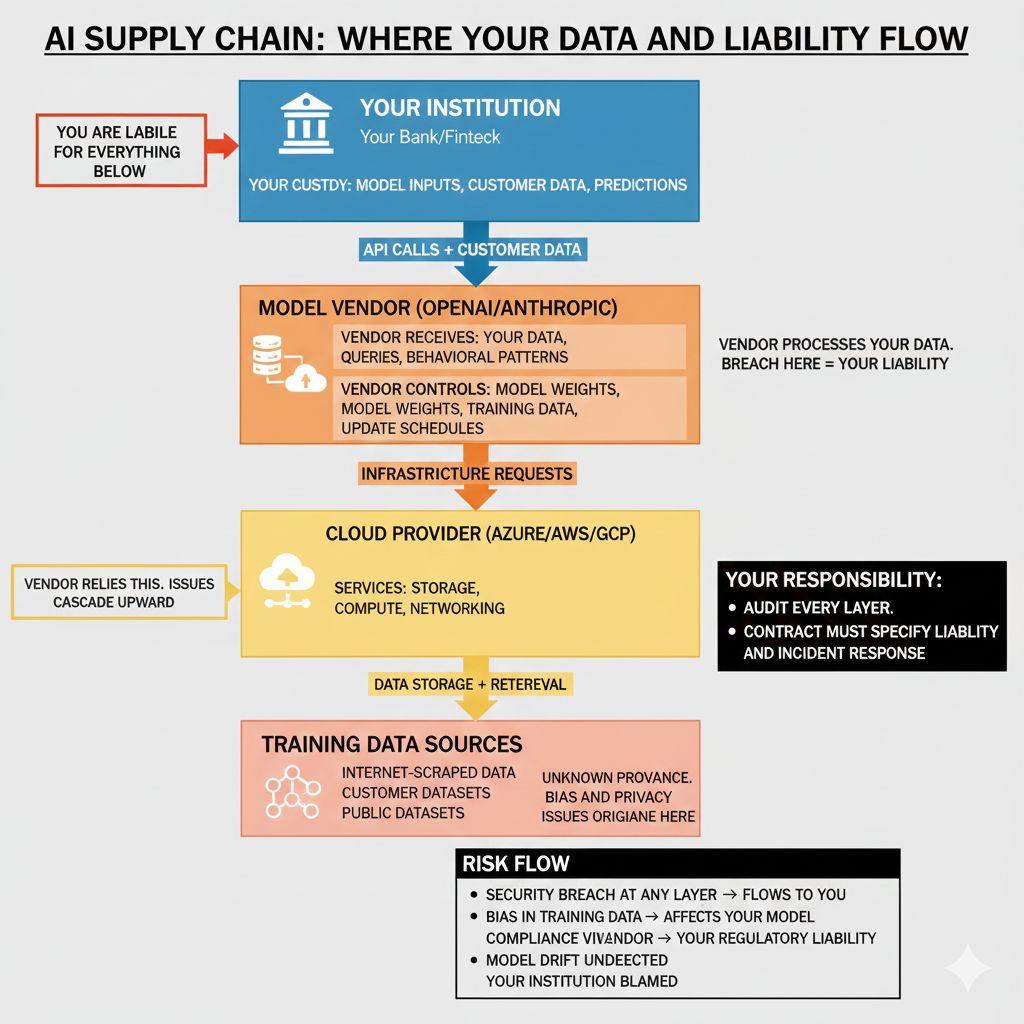
The Supply-Chain Risk Mindset
AI supply chains are complex:
Your Institution
↓
Model Vendor (OpenAI)
↓
Their Infrastructure Provider (Azure)
↓
Their Data Sources (Internet-scraped data, customer datasets)
↓
Third-party components (open source libraries with unknown provenance)A breach at any layer affects you. A bias in OpenAI's training data affects your model. An open source library vulnerability affects OpenAI's infrastructure.
Regulators expect you to trace this chain and assess risk at each layer.
Deep Dive: Building a Vendor Risk Framework
The Vendor Assessment Matrix
Before signing with any vendor, evaluate across eight dimensions:
Dimension 1: Data Handling
Question: Do you store my data after service ends?
Answer options: Delete after 30 days (good), Retain for machine learning (risky), Unclear (unacceptable)
BFSI requirement: Must have explicit deletion policy in contract
Dimension 2: Security Certifications
Question: What security standards do you meet?
Answer options: SOC 2 Type II (good), ISO 27001 (good), ISO 9001 only (insufficient), None (unacceptable)
BFSI requirement: At least SOC 2 Type II for any customer-facing vendor
Dimension 3: Audit Rights
Question: Can we audit your security practices?
Answer options: Annual third-party audits with results shared (good), Annual audit but no access (insufficient), No audit rights (unacceptable)
BFSI requirement: Contractual right to audit, or access to third-party audit results
Dimension 4: Incident Response
Question: How do you notify us of security breaches?
Answer options: Within 24 hours, documented response process (good), Within 72 hours (acceptable), Within 30 days (unacceptable)
BFSI requirement: 24-48 hour notification SLA in contract
Dimension 5: Model Transparency
Question: Can you explain your model's decisions?
Answer options: Explainability tools available (good), Feature importance available (acceptable), Black box, no explainability (risky for regulated decisions)
BFSI requirement: For credit/lending decisions, explainability is non-negotiable
Dimension 6: Bias Testing
Question: How do you test for bias in protected attributes?
Answer options: Regular testing with results shared (good), Testing done but not shared (insufficient), No formal testing (unacceptable)
BFSI requirement: Vendor must provide bias testing results for gender, race, age, income
Dimension 7: Jurisdiction & Compliance
Question: Where is data stored? What regulations do you comply with?
Answer options: GDPR, CCPA, HIPAA compliance certified (good), Data residency commitments (good), Multi-country data storage, unclear policies (risky)
BFSI requirement: Must match your regulatory jurisdiction
Dimension 8: Continuity & Exit
Question: What happens if you go out of business or we leave?
Answer options: Model export available, 90-day transition period (good), Data held hostage, long termination notice (risky), Unclear (unacceptable)
BFSI requirement: 6-month minimum transition period in contract
Score each dimension: Green (acceptable) / Yellow (negotiate) / Red (dealbreaker).
Template: Vendor Due Diligence Questionnaire
Before contracting, send vendors this questionnaire. Require specific, detailed answers—not marketing copy.
VENDOR RISK ASSESSMENT QUESTIONNAIRE
(To be completed before any contract negotiation)
SECTION A: DATA HANDLING
A1. Do you retain customer data after service ends?
Required answer: "No. All customer data is deleted within [X] days of service termination."
A2. Can your employees access customer data for any reason?
Required answer: "No. Data is encrypted. Access restricted to [specific reasons]. Logged and audited."
A3. Do you use customer data for training your models?
Required answer: "No. Customer data never enters our training pipelines."
A4. Where is customer data stored?
Required answer: "Specific geographic region(s). Customer data never leaves [region]."
SECTION B: SECURITY
B1. What security certifications do you hold?
Required answer: "SOC 2 Type II, ISO 27001, dated [year]. Third-party audit report available [yes/no]."
B2. What is your incident response time for security breaches?
Required answer: "Customer notification within [24/48] hours. Full incident report within [X] days."
B3. Have you experienced a security breach in the last 3 years?
Required answer: "Yes/No. If yes: [detailed description, customer impact, remediation]."
SECTION C: MODEL GOVERNANCE
C1. How is your model trained? On what data?
Required answer: [Detailed training methodology, data sources, dates]
C2. How do you test for bias against protected attributes?
Required answer: "Regular testing against age, gender, race, income. Testing results available quarterly."
C3. Can we audit your model's decisions on our data?
Required answer: "Yes. Explainability available. Sample audit reports available for review."
C4. How frequently do you update the model?
Required answer: "Updates [frequency]. Notification sent [advance days]. Rollback available."
SECTION D: COMPLIANCE & AUDITING
D1. What regulations do you comply with?
Required answer: "GDPR, CCPA, HIPAA, and [others]. Compliance certifications: [list with dates]."
D2. Can we audit your security practices?
Required answer: "Yes. Annual audit rights. Audit reports [shared with us / provided by third party]."
D3. How do you respond to regulatory requests for our data?
Required answer: "Immediate notification to customer. Legal hold honored. Compliance with [jurisdiction] requirements."
SECTION E: CONTINUITY
E1. What is your data export capability if we terminate?
Required answer: "Full data export in [standard format]. Available within [number] days of request."
E2. What notice period do you require for termination?
Required answer: "[X] days. Extended transition support available."Vendor answers become part of your due diligence file. Regulators review these during examinations.

BFSI-Specific Patterns
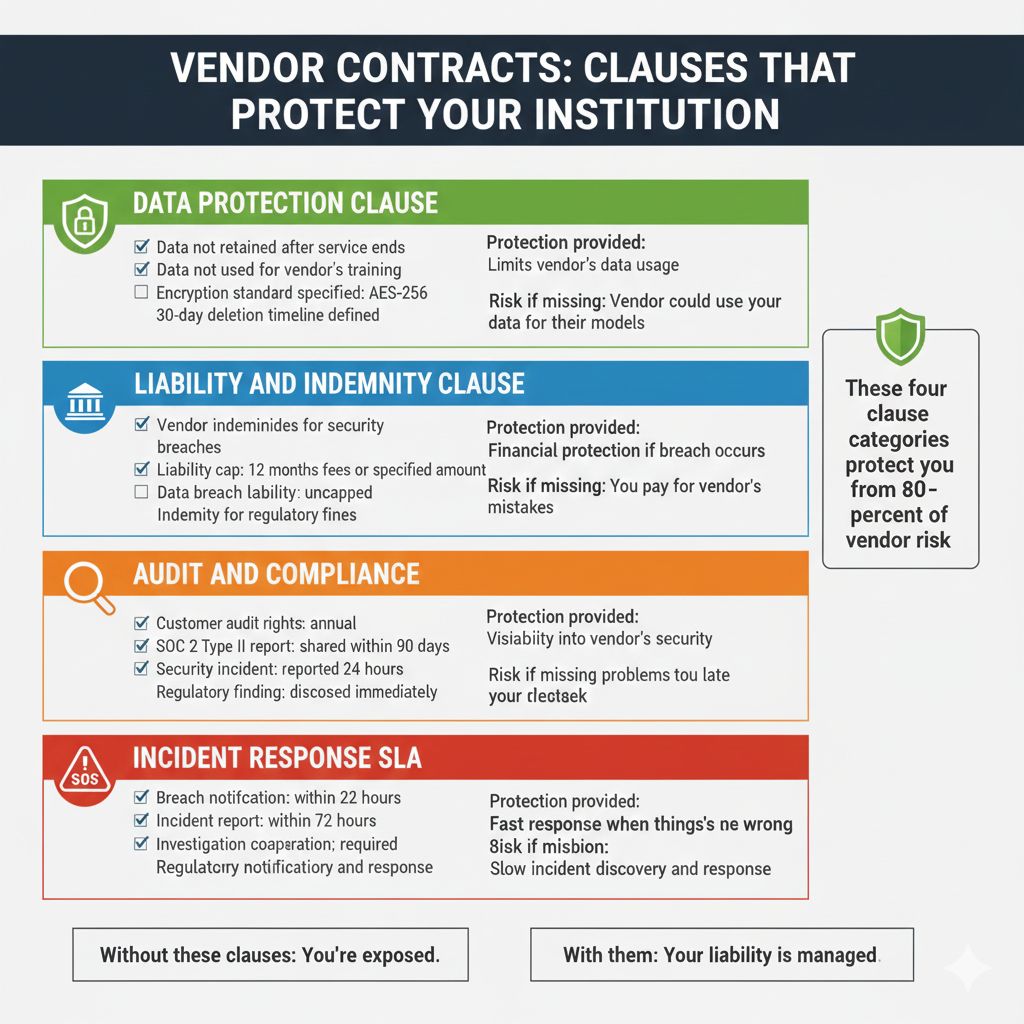
Pattern 1: Contract Language That Protects You
Standard vendor contracts favor the vendor. Your legal team must add protective clauses:
Data Protection Clause
"Vendor shall not retain, store, or use Customer data for any purpose except direct delivery of services."
"Customer data shall be deleted within 30 days of service termination."
"Vendor shall encrypt all data in transit and at rest with [minimum encryption standard]."
Liability and Indemnity Clause
"Vendor indemnifies Customer for breaches of Vendor's security practices."
"Liability cap: [amount] or 12 months of service fees, whichever is greater."
"For data breaches: liability cap does not apply."
Audit and Compliance Clause
"Customer has right to audit Vendor's security practices annually."
"Vendor shall provide SOC 2 Type II reports annually within 90 days of fiscal year end."
"Vendor shall notify Customer of any regulatory findings within 24 hours."
Incident Response SLA
"Vendor shall notify Customer of security incidents within 24 hours."
"Vendor shall provide incident report within 72 hours including: breach scope, customer impact, remediation steps."
"Vendor shall cooperate fully with Customer's incident investigation and regulatory notification."
Your legal team should negotiate these before signing. Pre-negotiated terms are standard in the industry.
Pattern 2: Ongoing Vendor Monitoring
Vendor risk doesn't end at contract signature. Ongoing monitoring is required:
Quarterly Reviews
Download SOC 2 audit reports
Review any security incidents reported
Verify data deletion logs (sample checks)
Check for model updates (notify compliance team)
Annual Reassessment
Re-run vendor risk questionnaire to check for changes
Review any regulatory findings against the vendor
Assess model performance for bias drift
Evaluate competitive alternatives (re-negotiate if better options exist)
Incident Escalation
If vendor experiences breach: Immediate investigation
What data was compromised?
Could it affect your customers?
Do you need to notify regulators?
If vendor updates model without notice: Escalate to compliance
If vendor's security certifications lapse: Escalate to procurement
Pattern 3: Multi-Vendor Strategy
Never rely on single vendor for critical models. Build redundancy:
Strategy: Use different vendors for different model components or maintain backup vendors.
Example: Fraud detection
Primary vendor: OpenAI for initial scoring
Backup vendor: Anthropic for validation
If primary vendor has outage/breach: Switch to backup within hours
Cost: Higher (paying for two vendors) Benefit: Resilience. If primary vendor fails, you don't lose model availability.
What Regulators Actually Want
From examiner conversations at banks:
❌ They don't want to hear:
"The vendor said it's secure"
"We have a contract"
"We rely on their audit reports"
"We didn't know about the incident"
✅ They want to hear:
"We completed comprehensive vendor due diligence questionnaire"
"We reviewed their SOC 2 Type II report before signing"
"We have contractual audit rights and exercise them annually"
"We monitor model outputs quarterly for bias or drift"
"We have incident response procedures with 24-hour notification requirement"
"We tested backup vendors and can switch within [X] hours if primary fails"
Practical checklist:
Vendor risk questionnaire completed and documented
SOC 2 Type II report reviewed (within last 12 months)
Audit rights established in contract
Incident notification SLA defined (24-48 hours)
Ongoing monitoring process documented
Backup vendor identified or redundancy strategy in place
Annual reassessment scheduled
Regulators will ask for your vendor file during examinations.
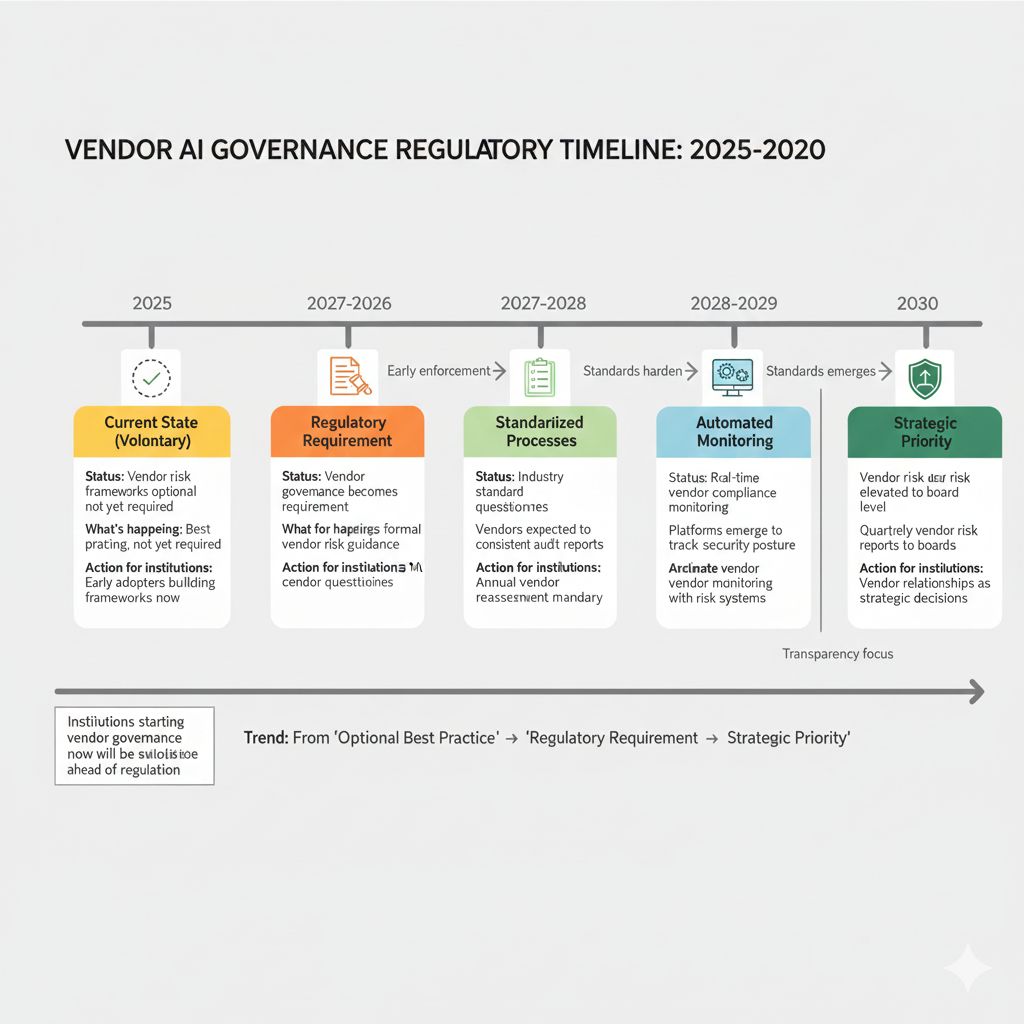
Looking Ahead: 2026-2030
2026: Vendor AI governance becomes regulatory requirement
Regulators publish formal frameworks for vendor risk assessment
Banks without documented due diligence face findings
Vendor questionnaires become industry standard
2027-2028: Automated vendor compliance monitoring emerges
Platforms that continuously monitor vendor security posture
Real-time alerts if vendor's compliance status changes
Integration with your risk systems
2028-2029: Vendor transparency standards improve
Pressure on vendors to open-source training methodology
Explainability requirements tighten (vendors must explain model decisions)
Bias testing results made public or shared under NDA
2030: Supply-chain risk becomes strategic priority
Third-party AI risk becomes as important as cyber risk
Boards receive quarterly vendor risk reports
Largest vendors consolidate (weaker vendors exit, leaving safer options)
HIVE Summary
Key takeaways:
Vendor risk extends beyond contract—regulators hold you accountable for vendor behavior even if you didn't build the model
Eight dimensions matter: data handling, security certifications, audit rights, incident response, model transparency, bias testing, jurisdiction, and continuity
Supply chains are complex—risk exists at multiple layers (model vendor → their infrastructure → their data sources). Audit every layer.
Due diligence questionnaire is your foundation—specific, detailed answers become your protection if issues arise later
Ongoing monitoring is mandatory—annual reassessments, quarterly security reviews, incident escalation procedures
Start here:
If contracting with new vendor now: Use vendor risk questionnaire. Get SOC 2 Type II report. Add protective clauses to contract before signing.
If already using vendors: Conduct initial assessment of current vendors. Document SOC 2 reports. Establish audit rights and incident notification SLAs.
If scaling vendor relationships: Build multi-vendor strategy. Identify backup vendors. Document monitoring procedures for compliance team.
Looking ahead (2026-2030):
Vendor AI governance becomes regulatory mandate (not optional best practice)
Automated compliance monitoring platforms emerge (real-time vendor health checks)
Vendors become more transparent (training data, bias testing, model explanations)
Supply-chain risk becomes board-level priority (quarterly vendor risk reports)
Open questions:
How to verify vendor claims about data deletion? (You can't physically audit their data centers)
When should you reject a vendor for bias or risk? (No perfect vendors exist)
How to maintain vendor relationships while treating them as adversarial for risk purposes? (Tension between partnership and skepticism)
Jargon Buster
Vendor Risk: Risk that external vendors' security practices, data handling, or operational failures cause harm to your institution. Includes data breaches, service outages, regulatory violations. Why it matters in BFSI: Regulators hold you liable for vendor failures.
Supply-Chain Risk: Risk that problems cascade from vendors' vendors (infrastructure providers, data sources, open source components). Why it matters in BFSI: A breach at vendor's cloud provider affects you. Bias in vendor's training data affects your model.
Due Diligence: Process of thoroughly investigating vendor before contracting. Includes questionnaires, security reviews, audit report reviews, reference checks. Why it matters in BFSI: Required by regulators. Documented due diligence protects you if issues arise.
SOC 2 Type II: Security audit certification verifying vendor's security controls. Type II = controls tested over time (usually 6-12 months). Why it matters in BFSI: Industry standard proof that vendor meets minimum security standards.
SLA (Service Level Agreement): Contract term specifying vendor's performance standards (uptime, response times, incident notification). Why it matters in BFSI: Defines what happens if vendor fails.
Data Residency: Physical location where data is stored. Why it matters in BFSI: Some regulations (GDPR, data sovereignty laws) require data stored in specific jurisdictions. Vendor must honor residency requirements.
Incident Response: Vendor's procedures for responding to security breaches (detection, notification, remediation). Why it matters in BFSI: Your regulatory obligations depend on vendor's incident response speed and quality.
Model Explainability: Ability to understand why a vendor's model made a specific decision. Why it matters in BFSI: For credit decisions, regulators require explainability. Vendor's black-box model is risky for regulated decisions.
Fun Facts
On Vendor Breach Liability: A major US bank contracted with an AI vendor for fraud detection. Vendor experienced a data breach affecting customer records. Bank was liable for breach notification (50K customers), credit monitoring (estimated $1M cost), and regulatory fines ($2M). Why? Regulators reviewed the bank's vendor contract and found: no explicit data deletion clause, no 24-hour incident notification SLA, no audit rights. Bank's lack of due diligence was the regulatory violation. The lesson: Your contract protects you or doesn't. Negotiate aggressively before signing.
On Hidden Supply-Chain Risks: A fintech used an open-source ML library as part of their vendor-supplied fraud model. Six months later, researchers discovered the library contained training data from millions of Equifax credit reports (the massive 2017 Equifax breach). The fintech's vendor didn't disclose this. Regulators investigated vendor supply chain and found the training data risk. Vendor faced lawsuits and reputation damage. Fintech was required to audit all vendor supply chains and disclose to customers. The lesson: Ask vendors about their upstream data sources. Supply-chain risk cascades.
For Further Reading
Federal Reserve Guidance on Third-Party Relationships (Federal Reserve Board, 2024) - https://www.federalreserve.gov/supervisionreg/srletters/sr2403a1.pdf - Regulatory requirements for vendor risk assessment and management. Required reading for understanding regulator expectations.
NIST Cybersecurity Supply Chain Risk Management (National Institute of Standards and Technology, 2024) - https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-161r1.pdf - US federal framework for supply-chain risk. Directly applicable to AI vendor risk.
SOC 2 Type II: What It Is and Why It Matters (AICPA, 2024) - https://www.aicpa.org/soc - Explanation of SOC 2 compliance. Required knowledge for evaluating vendor security certifications.
Vendor Risk Assessment Questionnaires (American Bankers Association, 2024) - https://www.aba.com/news-research/research-analysis/vendor-risk - Industry-standard questionnaire templates. Use as baseline for your vendor assessments.
AI Supply Chain Transparency and Governance (World Economic Forum, 2024) - https://www3.weforum.org/docs/WEF_AI_Governance_2024.pdf - Emerging frameworks for AI-specific vendor governance. Preview of where regulation is heading.
Next up: Week 6 Wednesday shifts to operational monitoring—distribution shift and model degradation. Using Evidently AI to detect when your model's behavior is changing over time and automatically triggering review processes before predictions go bad.
This is part of our ongoing work understanding AI deployment in financial systems. If you've negotiated vendor contracts and discovered contract language that protected you from vendor risk, share your templates.
— Sanjeev @ AITechHive
